9 tips for not getting spied on while traveling

Our phones and computers may be relatively secure, but nothing is particularly secure when up against state-sponsored hacking operations. Most companies and organizations have strict rules governing laptops and phones to prevent their data and intellectual property from being stolen or otherwise compromised. Often, they involve a list of countries to which burner devices are encouraged or required.
Corporate espionage is an enormous problem — especially when it’s done by other countries. Often, that country is China, and the theft of intellectual property is a major grievance in the current trade war. According to a CNBC survey of CFOs in March, one in five North American companies claim to have had their intellectual property stolen within the past year.
China isn’t the only source of trouble, however. There are many countries that engage in corporate cyber espionage – but rather than just simply avoiding travel to countries on the “high-risk” list, cybersecurity professionals would rather you change how you think about your security.
The right way to think about security
The most important thing to do before travel is to think about yourself and your own risk profile, cybersecurity experts Alex Hamerstone of TrustedSec and Michael Rohrs, Principal at Control Risks told Yahoo Finance.
“What do I have that someone else might want?” is the question that Hamerstone advises people to think about first. “The fact of the matter is a lot of surveillance can be automated, but as far as truly targeting someone, they can't target every single traveler,” he said. In other words, a corporate traveler presents a much different risk profile than someone on vacation.
Usually. Sometimes, it’s a little more nuanced — you may not realize that you could be a target. For example, if you work for a large company, it might have some sort of intellectual property worth taking. Even if you don’t work on something sensitive, one compromised device – your company-issued laptop or smartphone – can be enough to get a cyber foot in the door.
Understanding the country you’re going to is key. If you work for a tech company, you might want to be careful going to certain countries with records of IP theft or espionage.
Hamerstone says that a great guideline to follow is: you can't lose what you don't have. “You don't want to travel with devices loaded with information. Don’t take your everyday computer; take something different,” he said. “Some companies have loaner laptops specifically hardened to go overseas.”
The FBI has a list of “critical information” that it recommends people avoid bringing with them: Customer data, employee data, vendor information, pricing strategies, proprietary formulas and processes, technical components and plans, corporate strategies, corporate financial data, phone directories, computer access protocols, computer network design, acquisition strategies, marketing strategies, investment data, negotiation strategies, passwords.
If you’re unable to take a loaner device, you can always make a backup and remove things. And since phones can be had for cheap, it’s often worth getting a burner. And if you can use a VPN, which extends a private network to a public one, you should.
Important things to consider
Cybersecurity experts first advise people to find out the laws in the place they’re going to. Certain countries ban bringing encrypted devices in and out of the country or to specific countries. This can even include the U.S., as “exporting” an encrypted device to certain places could be a violation of U.S. sanctions.
In other countries, tools like encryption and VPNs may be illegal or regulated and could result in harassment from the government in countries like Belarus, Burma, China, Hungary, Iran, Israel, Kazakhstan, Moldova, Morocco, Russia, Saudi Arabia, Tunisia, and Ukraine, according to Texas State University. Even possessing a device that is encrypted poses a travel risk.
One cybersecurity expert said that being detained at the border for no other reason than that would be a “self-inflicted wound.”
Some countries are known to systematically monitor all information, like China, Russia, and Belarus. China is especially not shy about mentioning that it systematically monitors communications.
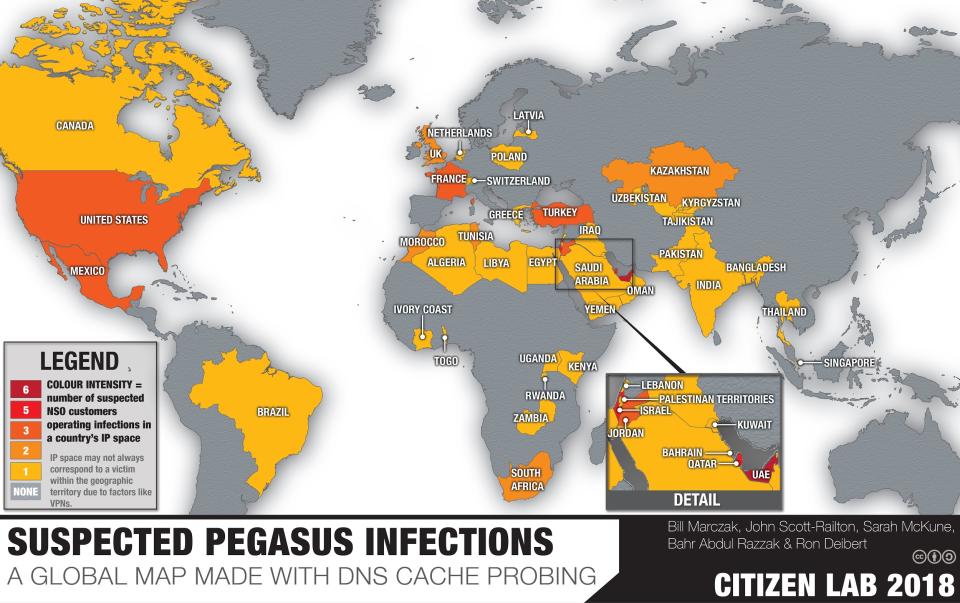
Another way to think about what countries might pose a problem: countries implicated in massive spyware campaigns, like NSO Group, an Israeli company that was mired in scandal for selling its Pegasus spyware technology to authoritarian countries. Mexico used it to spy on cartels, but also for government and industry surveillance, according to the New York Times.
According to Citizen Lab, which is part of the University of Toronto, 45 countries were involved in Pegasus.
9 good guidelines for traveling
Rohrs the cyber expert at Control Risks, a global specialist risk consulting firm, provided a handy list of nine guidelines for traveling:
1. Understand the encryption laws in the country you're traveling to. You're subject to local law. (You can ask your IT department, consult a cybersecurity expert, or even try Googling.)
2. The same is true of VPN services.
3. Only take the devices and the info on the devices you feel you absolutely need.
4. Find a balance between security and convenience.
5. Make sure all your apps and operating systems are updated and patched to the extent possible before you travel.
6.Try to avoid downloading new apps or updates to existing apps or operating systems while you're in foreign countries.
7. If you can use a VPN in your country of travel, we recommend it as opposed to relying on infrastructure in your hotel or the airport.
8. Have your devices scanned on your return before you connect them back to trusted home infrastructure like a home or office Wi-Fi.
9. Encrypt your devices — if you're allowed to have encrypted devices. If you leave them in a cab or hotel or airplane, they'll be bricked.
A list of countries
Every person will have their own individual list of countries in which they should exercise caution that’s separate from the list of 45 countries involved in Pegasus, for example. But a good place to start is with your employer. Often, the IT department has a list and protocol. Another great place: the U.S. government — which spies too — and its websites. Cybersecurity experts recommend looking at countries with sanctions and countries with travel advisories and looking for reported cyber threats.
Often, public institutions like colleges provide lists, unlike the IT department of a company. For example, the IT departments of Stanford and University of Colorado, Boulder have publiclists of “high-risk” countries for anyone to look at that are updated when necessary.
-
Ethan Wolff-Mann is a writer at Yahoo Finance focusing on consumer issues, personal finance, retail, airlines, and more. Follow him on Twitter @ewolffmann.
Hidden security risks caused by the latest technology
Large-scale credit card hackers back for the holiday season, ex-FBI investigator says
Joining the top 1% just got more difficult, IRS data reveals
The downside to living longer: Running out of money
Social Security phone scams are now a greater threat than IRS scams
How to know if your next flight is on a 737 Max
The 2020 Social Security increase falls short
Read the latest financial and business news from Yahoo Finance
Follow Yahoo Finance on Twitter, Facebook, Instagram, Flipboard, LinkedIn, YouTube, and reddit.