How to stop cyberattacks crushing cities across the US
Cities and states across the U.S. are facing an increasing number of cyberattacks from individuals holding important government data hostage and demanding huge sums of money for its safe return.
The attacks, which involve a type of malware called ransomware, have become more frequent and destructive in recent years, with several high-profile attacks hitting cities from New Jersey to California. And the price tag to recover from these attacks can easily eclipse the million-dollar mark.
Just last month Lake City, Florida paid $460,000 in ransom to get its systems back, and Baltimore, Maryland is expected to pay $18 million to repair its infected infrastructure, despite not paying a ransom.
"The bad guys will always be one step ahead," explained University of Maryland, Baltimore County cybersecurity professor Richard Forno. "And we should never expect there to be total security. What we need to do is plan."
These attacks can force entire governments offline. Citizens can’t pay bills, developers can’t get work permits, and police have seen important investigations slowed.
Entire governments left offline
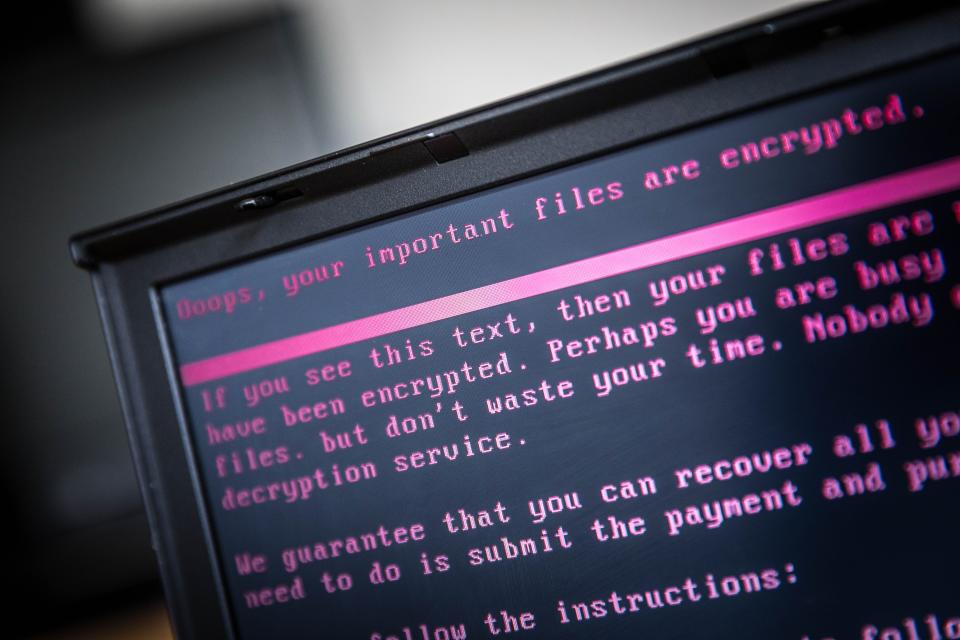
Ransomware is a form of malware that works its way into computer networks and locks down files and folders using data encryption. The most common way for an infection to take hold is via a simple email. Hackers use social engineering techniques to trick users into opening emails and clicking on links or downloading files that contain the malware. From there, the infection can spread across entire networks with ease, encrypting files and blocking access to them.
There's no way to unencrypt a locked file or database without the proper key. And, unfortunately, only the attacker holds it. That's where the ransom comes in. In exchange for anywhere from hundreds to thousands of dollars, usually paid in bitcoin, the attackers promise to provide the key that will unlock a victim's files.
There isn't one single form of ransomware. And locating the attackers is difficult, since they can mask their locations online. A number of ransomware variants exist in the wild, with an array of capabilities. Some even give cybercriminals a way to spy on networks to determine how large of a ransom they can demand.
One of the most dangerous versions is based on a National Security Administration tool used to hack into Windows PCs that was stolen by a hacker collective called The Shadow Brokers. That tool, called EternalBlue, has since spread across the world and has been employed in a number of attacks.
"The more sophisticated ransomware variants out there, we do see them doing reconnaissance on a network," explained FBI supervisory special agent Adam Lawson.
According to Lawson, who works in the FBI's Major Cyber Crimes Unit, some versions of ransomware will do significant research on a victim as they move around a network, and identify what they want to encrypt. If the attackers recognize they've latched onto a significant target, they'll demand a larger ransom to unlock the files.
In recent years, attackers have seen increased success in hitting municipalities across the U.S. And the attacks on municipalities are accelerating, according to Allan Liska, senior solutions architect at Recorded Future, which produced a study on ransomware attacks on U.S. cities.
Some attackers know exactly what cities they want to attack and move on them, explained Thomas MacLellan, director of policy and government affairs at Symantec. Other attackers aren't specifically targeting city and state governments, but instead, happen upon municipal governments and squeeze them for cash.
"It appears to be an unfortunate coincidence that city and states happen to use a lot of tools that are currently being targeted by ransomware actors," Liska explained. "For example, city governments appear to rely heavily on Remote Desktop Protocol for remote access; ransomware attackers are currently heavily targeting RDP as a point of entry.
"Once inside the network, these attackers then move around learning the network, understanding the different systems, and then will deploy the ransomware simultaneously across dozens or hundreds of systems.”
According MacLellan, attackers can dwell within a network for 180 days to 190 days poking around to determine the best way to launch a successful attack.
The result: Cities knocked back decades into the past, forced to rely on traditional pen and paper recordkeeping, and a delay in overall services.
Offline for weeks
The most high-profile incident of a ransomware attack on a city is the current infection roiling Baltimore, Maryland. The city was first hit with a ransomware attack in May, and according to The Baltimore Sun, some services were still offline as of last week.
The attack knocked out the city's credit card services, locked employee email accounts, and put a hurting on its real estate market thanks to the fact that property transfer services were down.
Then there was the attack on Lake City, Florida, which saw the city cut off from email and phone access.
"We had no telephone, no email, everything at the police department was still fine, but the entire city pretty much had no phone service," Lake City Public Information Officer, Sergeant Mike Lee explained.
The list of affected cities is long: Riviera Beach, Florida; Allentown, Pennsylvania; Plainfield, New Jersey; Cleveland, Ohio; Grant County, Oregon; Denver, Colorado; Atlanta, Georgia.
Recorded Future's Liska found reports of ransomware attacks hitting municipalities in 48 states and the District of Columbia since 2013. But since many towns and cities don't report ransomware attacks, as they're seen as more of an IT problem than a criminal act, there are no firm estimates for such incidents.
According to the FBI's Internet Crime Complaint Center, there were 1,493 official victims of ransomware in 2018. That number, though, only accounts for the number of victims who reported their attacks directly to the ICCC. The attacks cost users $3.6 billion. But again, that number is likely well below the reality of the situation.
The FBI explains that the $3.6 billion figure only accounts for direct reports to ICCC, and not to FBI field offices. It also can't take into account the cost of ransoms paid by consumers who didn't report the attacks. On top of that, the FBI states that the cost doesn't include "estimates of lost business, time, wages, files, equipment, or any third-party remediation services acquired by a victim."

Proof of that lies in the fact that Baltimore alone estimates that it will cost more than $18 million to get all of its systems back online. And that's without paying a ransom. Lake City, Florida, paid the attackers to take back control of its systems, which cost $460,000, or the equivalent of 42 bitcoins at the time of the attack.
And while experts like Forno and Lawson advise against paying ransoms, Mike Lee of the Lake City Police Department explained that it wasn't the town’s call to pay the cost of the ransom. Instead, it was the city's insurance company that paid off the attackers, after reasoning that it would be cheaper to do so than spend thousands more trying to recover backups of the locked data.
Stopping the attacks
Putting a stop to these kinds of ransomware attacks comes down to municipalities following best security practices. Lee explained that following the ransomware attack on Lake City, the town has invested in additional security measures, and is training staff on what kind of emails and links people should and shouldn't click on.
The main way for governments to protect themselves is to ensure that their systems have the latest security updates, and back up their data so they can use it as a means to restore their files if they're locked up.
There are other kinds of attacks, called zero-day attacks, which are almost impossible to protect against. Those attacks use previously unknown vulnerabilities in operating systems like Windows that are able to give them the ability to launch attacks that can't be stopped by patches.
In the end, the best way to avoid being hit by a malware attack is prevention. Don't open emails from people you don't know, never click on suspicious links, and ensure you have all of your data backed up.
More from Dan:
Zuckerberg defends Facebook's decision to keep up Pelosi ‘deepfake’ video
Lenovo’s and Google's Smart Alarm Clock might make you hate mornings less
Tim Cook on tech: ‘If you built a chaos factory, you can’t dodge responsibility for the chaos.’
Email Daniel Howley at [email protected]; follow him on Twitter at @DanielHowley.
Follow Yahoo Finance on Twitter, Facebook, Instagram, Flipboard, SmartNews, LinkedIn,YouTube, and reddit.
