Why leaked NSA hacking tools are not like stolen Tomahawk missiles

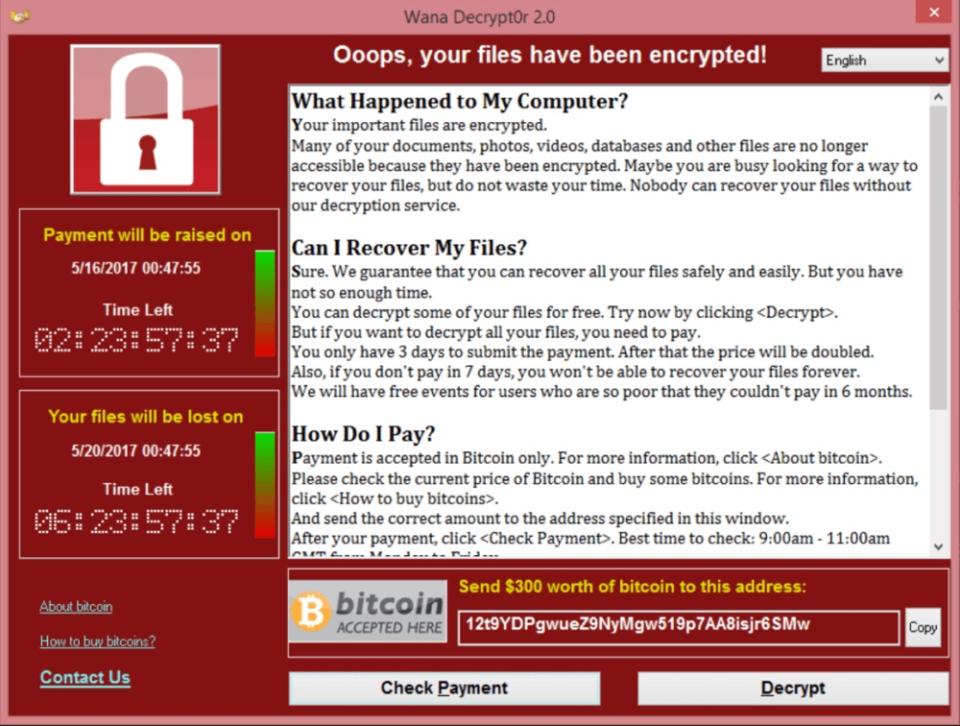
Last week a malicious computer worm dubbed WannaCry 2.0 began attacking older, unpatched versions of Microsoft operating systems, infecting hundreds of thousands of systems with ransomware that held user data hostage in exchange for Bitcoin payments.
The cyberattack used code from a powerful National Security Agency tool called EternalBlue, which a mysterious group of hackers known as The Shadow Brokers leaked earlier this year. Tech companies have been quick to blame the NSA for finding and exploiting vulnerabilities in commercial products like Windows, to say nothing of losing them.
On Sunday, Brad Smith, Microsoft’s (MSFT) president and chief legal officer, argued that an “equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen.”
The next day, Former NSA contractor Edward Snowden, speaking via video chat to the K(NO)W Identity Conference in Washington D.C. from an undisclosed location in Russia, repeated Smith’s argument.
“An equivalent scenario to what we’re seeing happening today would be conventional weapons, produced and held by the U.S. military, being stolen, such as Tomahawk missiles,” Snowden said while describing Smith’s letter to a crowd less than a mile from the White House.

U.S. officials acknowledge that the NSA deserves scrutiny about protecting tools it develops to collect foreign intelligence. “They’ve absolutely got to do a better job protecting [the hacking tools],” General Keith Alexander, head of the NSA from 2005 to 2014, told The Washington Post. “You can’t argue against that.”
However, the Tomahawk analogy may be a stretch. Dave Aitel, a former NSA research scientist and CEO of the cybersecurity company Immunity, explained why hacking tools are not like bombs.
“The very first thing is you can steal a Tomahawk missile from me, but you cannot steal it from me without me knowing you’ve stolen it,” Aitel said. “And of course, you can steal an exploit or other intellectual property from me and I may never find out. Another is that two people can have [the same exploit] at the same time.”
Aitel, who specializes in the offensive side of cybersecurity, added that “deep down, the biggest difference is that you have to learn a lot about exploits to protect yourself, and I don’t really have to learn a lot about Tomahawk missiles to protect myself from Tomahawk missiles.”
Nevertheless, the analogy has been relatively well received. Travis Jarae, CEO and Founder of One World Identity, which hosted the conference in Washington, and paid a speakers bureau to digitally host Snowden, said that the Tomahawk analogy is “not wrong” given the contemporary threat environment.
“Warfare is digital,” explained Jarae, who was previously Global Head of Identity Verification at Google. “We spy on people digitally … I thought it was a little aggressive to compare it to a missile, but [government hacking] is very damaging.“
Aitel noted that it makes sense why Smith and others in the tech business would make that argument.
“[Brad Smith’s] job is to create favorable economic conditions for Microsoft at a strategic level, and if he pressure governments to stop using exploits, then that helps him from a PR perspective,” Aitel said. “It doesn’t help the users because people are still going to have exploits. That’s always going to be true.”

Snowden also echoed Smith’s criticisms of the U.S. government’s decision to develop secret software exploits, telling the audience at the K(NO)W Identity Conference that secret government exploits are a problem, and the NSA should have voluntarily revealed the EternalBlue exploit long ago.
But other former NSA officials have pushed back against that idea, telling the Washington Post that EternalBlue netted an “unreal” foreign intelligence haul that was like “fishing with dynamite.”
“Edward Snowden knows full well the value of the signals intelligence program — and that includes the NSA’s hacking — to our national security,” Aitel said. “This is not for play. They’re not building exploits for fun. It’s not a hobby. It’s for distinct and important national security needs.
“So when he says ‘Give up your exploits,’ he essentially is saying, ‘We don’t need signals intelligence,’ which we do.”
Ultimately, according to Aitel, companies like Microsoft placing the blame on the NSA with crude analogies equating NSA hacking tools to U.S. cruise missiles only serves to muddy the larger debate.
“The bigger issue is Brad Smith and Microsoft, who continue to insist that everything fall their way in terms of how vulnerabilities are handled, which I don’t think helps the conversation around cybersecurity,” Aitel said. “There are a lot of very interesting things in cybersecurity that don’t involve Microsoft’s bottom line, and those are worth talking about.”
READ MORE:
The simple reason so many companies were hit by the WannaCry 2.0 ransomware
As tensions rise with Russia, U.S. colleges still pay for Snowden speeches
No, your Apple computer isn’t immune from ransomware
‘Risk’ director discusses the ‘tragedy’ of Julian Assange and WikiLeaks
